Top uses for Hydra in CTF challenges. Learn how to use Hydra to unlock Linux Capture the Flag events. Which password List to use.
Author: tomkraz
Linux CTF Cheatsheet for budding Pen-testers or red team members. There are many cheat sheets but here I go through common examples.
Data Repatriation is over looked by most companies. There should always be a strategy to bring your data back. In the long run its cheaper!
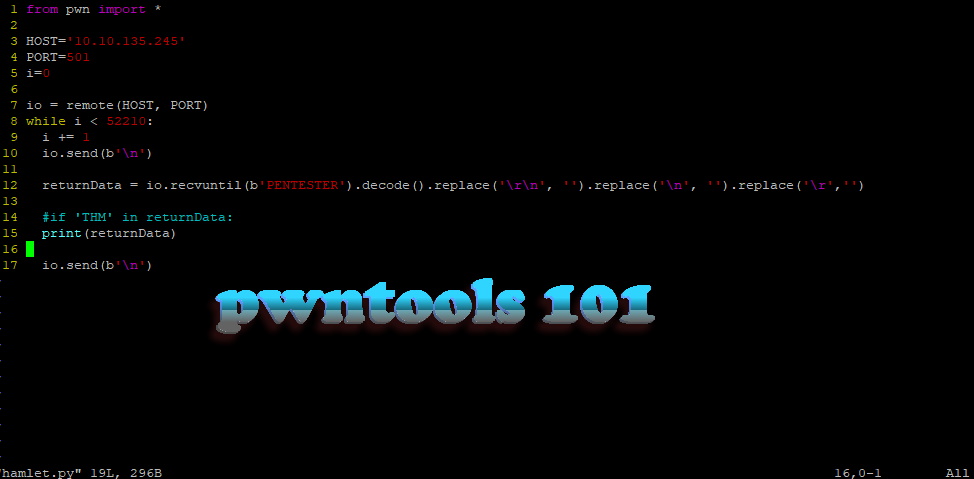
What is pwntools. The python module pwntools is a collection of tools developed to be used for CTF challenges. According to the website pwntools is…
Installing DVWA in Docker. Damn Vulnerable Web Application (DVWA) is a super useful learning tool for the budding Ethical Hacker or Pen Tester.
Background The free CTF Challenge web site “hackmyvm.eu” have an other medium level vm called ‘Corrosion3‘ for us to download, enumerate and get some flags.…
These are my list of the best tools I’ve come across for Pen-Testing , CTF Challenges and Ethical Hacking resources. Some of these are affiliate…
hackmyvm hotel is a CTF Challenge room requiring multiple levels of enumeration required. Read along this write-up to complete successfully.
Often in CTF (Capture the Flag) challenges we we come across FTP services running. Use this write-up to identity the main risks.
Netlas is a search engine for devices connected to the internet.