Getting started with Nessus, run your first Vulnerability scan. Nessus is a powerful Enterprise Grade tool, but don’t let that stop you.
Tag: CTF
Install Nessus with Docker and run a network scan. Nessus is a proprietary Vulnerability Scanner and can be deployed with Docker
TShark is a command line version of Wireshark. Learn tshark basics and improve your network and Linux skill.
While doing a CTF Challenge recently from hackmyvm.eu called pingme, I managed to get root access to the system, but not at all in the…
The free CTF Challenge web site “hackmyvm.eu” have an other easy level vm called ‘comingsoon‘ for us to download, enumerate and get some flags. This…
Burpsuite, the ever popular tool for Capture the flag Challenges and Ethical Hacking. Join me while I try to describe some of the features in 5 minutes.
Prepare a Docker lab for learning Ethical Hacking, Pen-testing and CTF challenges. Create a ftp, ssh and Wordpress containers.
Top uses for Hydra in CTF challenges. Learn how to use Hydra to unlock Linux Capture the Flag events. Which password List to use.
Linux CTF Cheatsheet for budding Pen-testers or red team members. There are many cheat sheets but here I go through common examples.
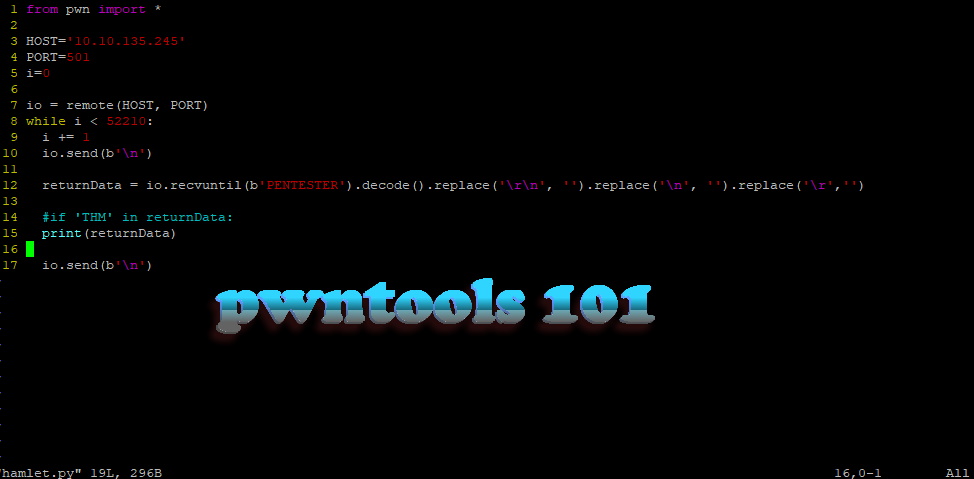
What is pwntools. The python module pwntools is a collection of tools developed to be used for CTF challenges. According to the website pwntools is…